User Key Management - S/Notify for Confluence
Please note that we've decided to move our support portal to help.savignano.net to to further improve the services for our customers.
The updated version of this page can be found at https://help.savignano.net/snotify-email-encryption/user-key-management-s-notify-for-confluence
Orange colored text describes functional differences in previous 3.x releases
Under this configuration entry, the public PGP keys or S/MIME certificates for Confluence users are managed. They are used for the encryption of outgoing emails.
For this, you will find the following configuration options:
Global User Key Management
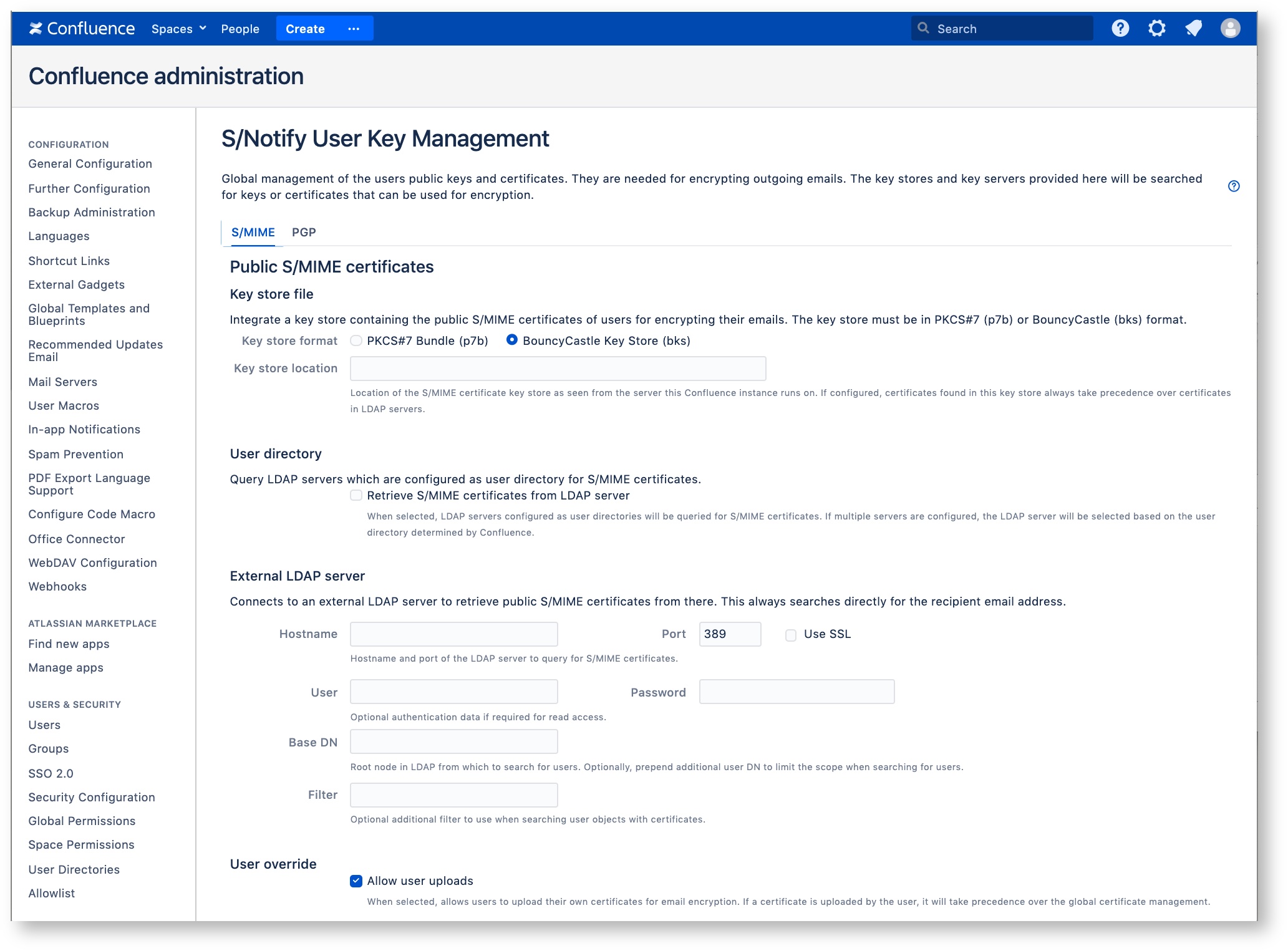
S/MIME
Key store file
In this section of the S/Notify configuration settings, you can optionally provide a global key store containing the certificates to be used for S/MIME email encryption.
Note that, due to the nature of asymmetric encryption, S/Notify requires only public certificate keys from the key store. As a consequence, a password is not required for access to the key store.
Key store format
The key store file must be in either of the following two formats:
- PKCS#7 (recommended)
This format is a common format used to export and transmit public certificates. It can hold multiple certificates and is therefore often referred to as a p7 bundle – hence the commonly used file suffix p7b. It is defined in RFC 2315. Note that the file needs to be in DER encoded (binary) format. - BouncyCastle
This format is usually represented by a file suffix of bks. It is supported mainly for backward compatibility reasons. The key store must be a BKS type BouncyCastle key store. For details on how to create such a key store, please refer to S/MIME Certificate Keystore.
Prior to version 3.1, the PKCS#7 format was not supported.
Key store location
Provide path and file name of the certificate key store, as seen from the server your Confluence instance runs on.
User directory
Prior to version 3.5, this section was named LDAP server. It was renamed to avoid confusion with external LDAP servers.
If enabled, S/Notify will use the LDAP server from the Confluence user directory the user is associated with, if applicable.
This setting requires that an LDAP server is used as a Confluence user directory, and that the user is found in this directory. S/Notify will then query the user's S/MIME certificate from the LDAP server in the following order and format:
Attribute | Format | Reference |
|---|---|---|
| userSMIMECertificate | PKCS#7 (p7m) signed message format with single certificate or certificate chain | RFC 2315: PKCS #7: Cryptographic Message Syntax |
| userCertificate | DER binary (base-64 encoded) or PEM (ascii encoded) single X.509 certificate | RFC 4523: LDAP Schema Definitions for X.509 Certificates |
Note that if both, key store and LDAP server are used, certificates found in the key store will take precedence over those on the LDAP server.
External LDAP server
S/Notify can optionally search for S/MIME certificates on an external LDAP server (outside Jira's configuration).
Personal Identifiable Information
Note that, in order to retrieve a user's S/MIME certificate, their email address needs to be sent to the server. If the LDAP server is outside your company's own infrastructure, you may be required to inform your users about this use of their email address, depending on your and/or your users jurisdiction. Legislation around personal identifiable information (PII) varies across different jurisdictions (GDPR, HIPAA, PCI etc.), so please check what applies in your case.
Hostname
The domain of the LDAP server, excluding the protocol part.
Port / SSL
The port served by the LDAP server. Usually 389 or 636 for SSL enabled connections (recommended).
User / password
Optional. Only if the server requires authentication.
Base DN
Most LDAP servers require to provide the Base DN of the root node to search from. Optionally, any additional DN can be prepended to limit the search scope (and thus improve speed).
Filter
Optionally, a filter can be provided to limit the search to specific objects. The filter will be added to the default filter that is used to search for objects with the email address being processed (mail=emailAddress).
Prior to version 3.5, external LDAP servers were not supported.
User override
When Allow user certificates is checked, users are allowed to upload their own S/MIME certificates in the user profile. If a suitable certificate is provided in both, the global key store and the user profile, the one from the user profile will be used.
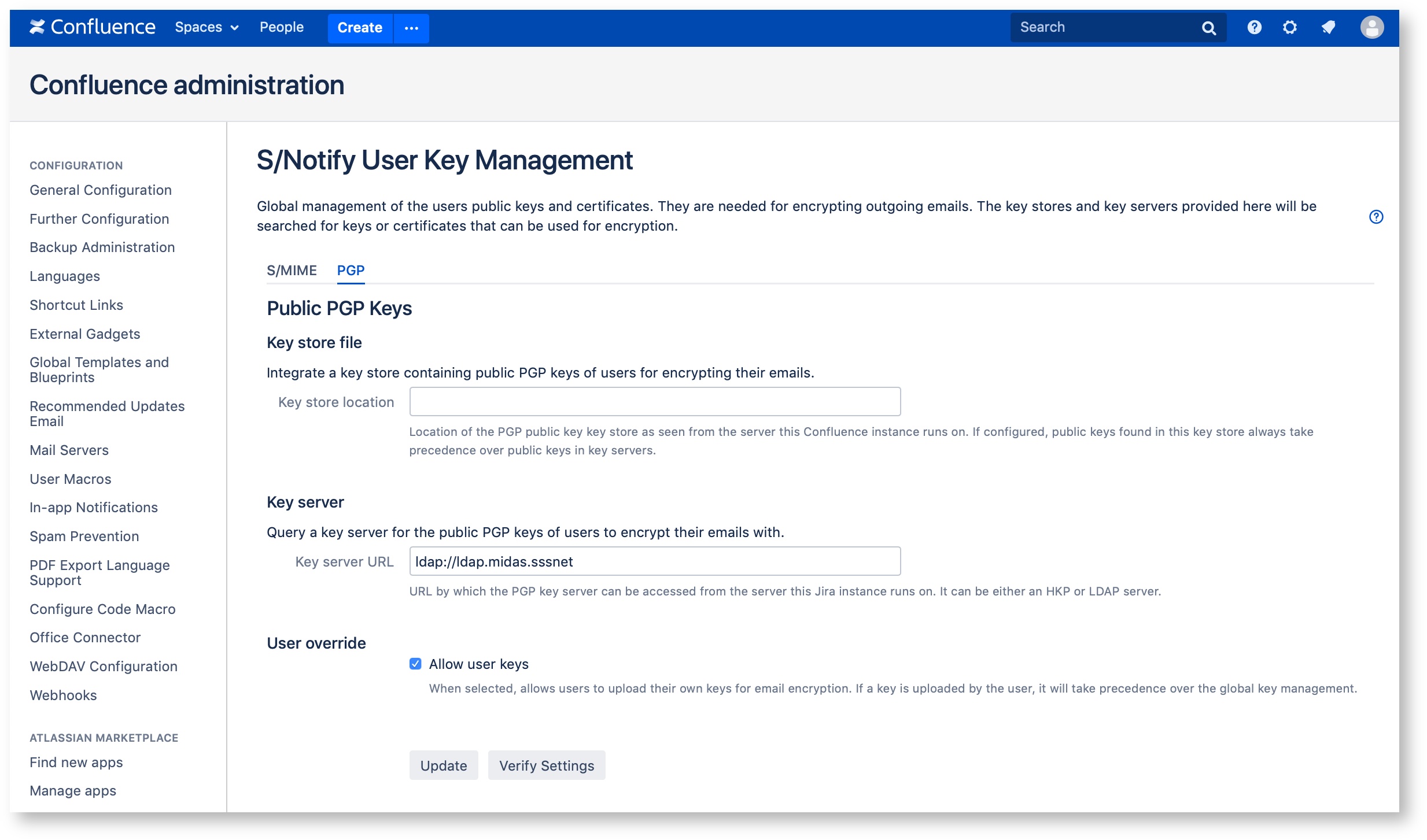
PGP
Key store file
In this section of the S/Notify configuration settings, you can optionally provide a global key store containing the keys to be used for PGP email encryption.
Note that, due to the nature of asymmetric encryption, S/Notify requires only public keys from the key store. As a consequence, a password is not required for access to the key store.
Key store format
The key store file must be in either of the following two formats:
- ASCII-Armored
This format is a common format used to export and transmit public keys. It is, as the name implies, encoded fully in ASCII. Usual file endings are: asc, txt - PGP Binary
PGP binary file format. Usual file endings are: pgp, gpg, pkr
Keybox format
Note that the new keybox format (kbx) is not currently supported. If your GPG installation uses the keybox format, you must export it in one of the above formats in order to use it as a key store for S/Notify.
Key server
In this section of the S/Notify configuration settings, you can provide an URL to a PGP key server that will be searched for PGP keys to encrypt with.
Personal Identifiable Information
Note that, in order to retrieve a user's PGP key, their email address needs to be sent to the server. If the key server is outside your company's own infrastructure, you may be required to inform your users about this use of their email address, depending on your and/or your users jurisdiction. Legislation around personal identifiable information (PII) varies across different jurisdictions (GDPR, HIPAA, PCI etc.), so please check what applies in your case.
Key server location
Provide the URL to an HKP or LDAP key server. Use this setting to administrate PGP keys centrally instead of requiring each user to provide his or her own PGP key.
For HKP servers, use either http or hkp or https or hkps URL schemes to provide the PGP key server URL.
For LDAP servers, use either ldap or ldaps URL schemes to provide the PGP key server URL. LDAP servers are required to follow the structure as in Broadcom's PGP Universal Server, also supported by GnuPG.
For more information about public PGP key servers, see PGP Key Retrieval.
Note that this is not a required setting. If left empty (or erased), a key server will just not be used, and only user profiles PGP keys will be used.
Prior to version 3.4, only HKP based key servers were supported.
Outbound Proxy
If your Confluence is operated behind an outbound proxy that limits access to external domains, please make sure that the key server URL is added to the exception list, so the key server can be accessed.
For details on operating Confluence with an outbound proxy, please refer to the Atlassian documentation.
User override
When Allow user keys is checked, users are allowed to upload their own PGP keys in the user profile. If a suitable PGP key is provided in both, the global key server and the user profile, the one from the user profile will be used.
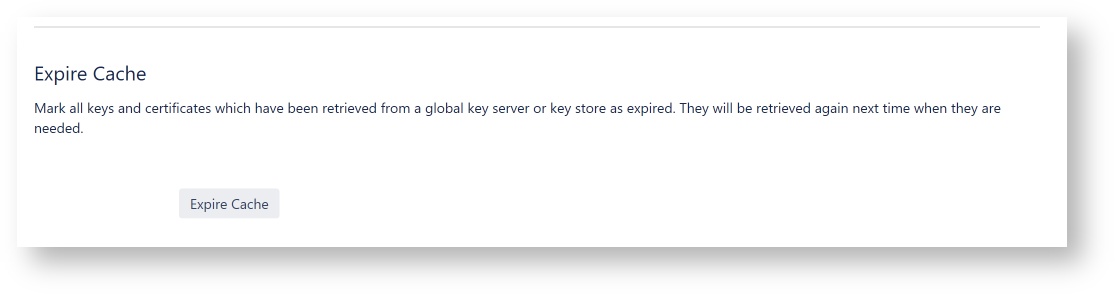
Expire Cache
When this button is hit, all S/MIME certificates and PGP keys from the key store or key server are marked expired. Consequently, next time when an S/MIME certificate or PGP key is needed for encryption, they will be retrieved freshly from the key store or key server. Use this when you want S/Notify to reload certificates and keys.
If you change the key store location or key server url, this also expires the cache, so after that, all certificates and keys will be retrieved from the new key store or key server.
Note that the key store or key server is not queried, if the user has provided an S/MIME certificate or PGP key in his or her user profile.
Related articles
The S/Notify Email Encryption apps are brought to you by savignano software solutions, a small yet savvy IT solutions company in Germany. Click here for legal information.