| Info |
|---|
Please note that we've decided to move our support portal to help.savignano.net to to further improve the services for our customers. The updated version of this page can be found at https://help.savignano.net/snotify-email-encryption/encryption-settings-s-notify-for-jira |
Orange colored text describes functional differences in previous 3.x releases
...
When enabled, emails that are sent to users to recover access to Jira will always be sent unencrypted. Use this if your users should be able to reset their password in Jira. Note that this might not be useful if user credentials are managed outside of Jira.
When enabled, the following types of emails are exempt
- initial user invite
- request to reset the password
- account email confirmation
In Jira Service Management, this also applies to customers.
Prior to version 3.6, this option was not available.
...
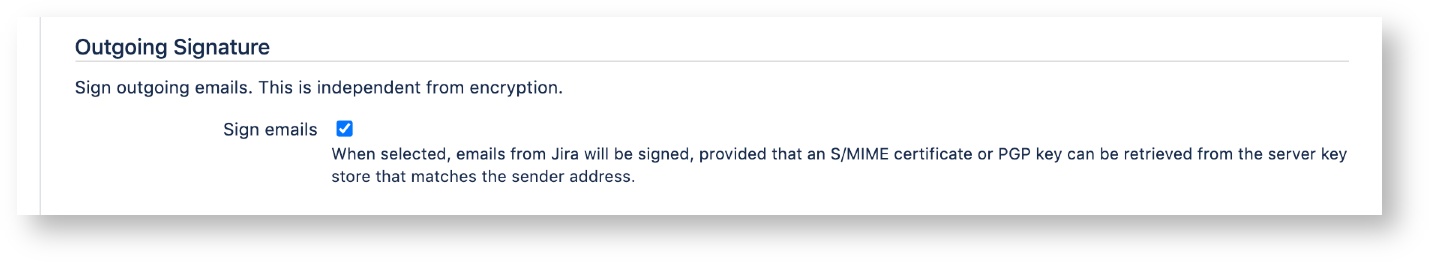
This section allows you to sign outgoing emails.
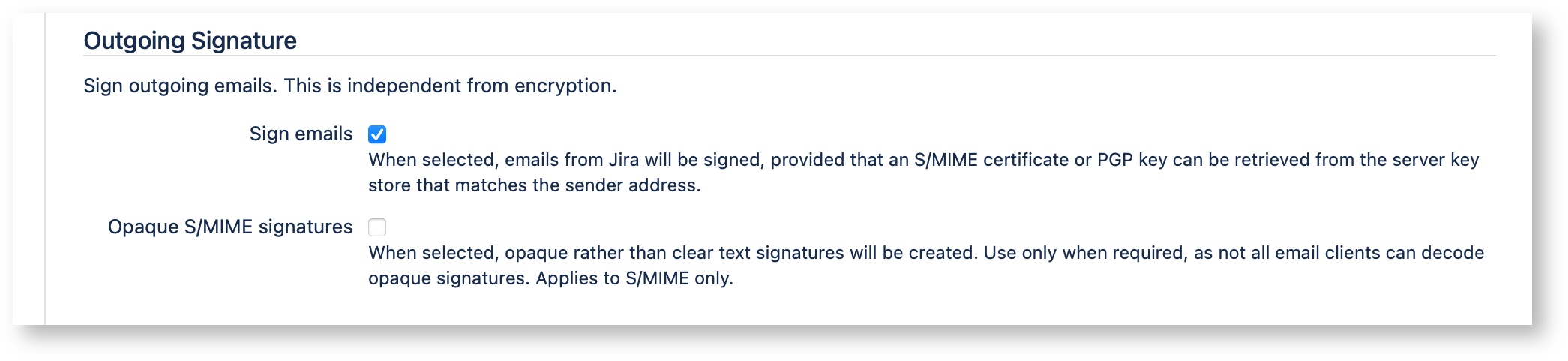
Sign emails
When selected, S/Notify will attempt to sign all outgoing emails using an appropriate PGP key or S/MIME certificate retrieved from the key store(s) provided in Server Key Management. The PGP key or S/MIME certificate must be issued for signing purposes as well as for the sender email address. This is usually the email address configured under Outgoing Mail, but keep in mind that you might be using additional project specific email addresses. If you use multiple sender addresses, you can either use multiple keys or certificates, or one that has been issued for multiple email addresses (or even a mixture of both variants).
...
Prior to version 3.1, intermediate certificates were not included.
Opaque S/MIME signatures
When selected, S/Notify uses so-called opaque S/MIME signatures instead of detached or clear-text signatures. With opaque signatures, the message contents is encoded and cannot be read in email clients that do not support opaque signatures.Therefore, we recommend not to use opaque signatures unless necessary.
Some email servers, especially MS Outlook servers, are known to reformat emails. This will break detached signatures, because the receiving email client will (rightly) complain about the message having been tampered with. This problem can only be avoided by the use of opaque signatures.
Prior to version 4.0, opaque signatures could only be enabled via the Advanced Settings dialog.
Incoming Email
If incoming emails are encrypted, S/Notify will always attempt to decrypt them. However, this section allows you to configure additional processing of incoming emails.
...
| Issue description or comment was created from incoming email | |
| Email was encrypted, has been decrypted (encryption type preceding this symbol) | |
| Email was encrypted with a non-preferred cipher, yet has been decrypted* (possible downgrade attack, optionally disable under Advanced Settings) | |
| Email was encrypted with a key that was not found in the server keystore, so could not be decrypted | |
| Email was encrypted, but could not be decrypted for any other reason (refer to log file for details) | |
| Email was signed, and signature has been successfully verified | |
Email was signed, but certificate issuer could not be verified | |
| Email signature verification failed, so email may have been tampered with |
* This category was not available prior to version 4.0
Remove signatures
When selected, S/Notify will remove email signatures (if exist) from all incoming emails after they have been verified. Use this option to avoid getting these signature files attached to the Jira issues over and over again.
...